Hijacking an Abandoned Careem S3 Bucket
Hi All,
This story took place last year, and I thought it would make a great case study on leveraging broken links. Additionally, it includes a funny anecdote that highlights how I find security issues wherever I go.
Introduction
Last year, I traveled to Dubai to explore the city and meet some good friends: Yasser, Ahmed, and Ayoub.
I am a loyal Careem user and rely on it whenever I travel, including in Iraq. When it was time to return home, I ordered a taxi through the Careem app. I waited as the driver approached my hotel. I grabbed my bag and stood on the sidewalk, hoping he would spot me since it was early morning and the streets were empty. He saw me but didn’t move. I waved at him, but he drove off and canceled the ride, marking that I hadn’t shown up.
Frustrated, I ordered another ride as I needed to get to the airport as soon as possible. The new driver was nearby, so I didn’t have to wait long. However, I later discovered that the Careem app had already charged me a fee for the ride I didn’t take!
When I returned home, I submitted a complaint about the incident. Careem’s customer support called me, and I explained what had happened. They apologized and refunded the fee. Heeey!
Technical Details
A while later, I received an email from their customer support asking if I was satisfied with my recent interaction with their team. I noticed a broken link in the email and was surprised that they hadn’t caught it.
I used the browser’s inspect element tool to examine the broken link. The link was:
<img alt="Careem" title="Careem" src="https://ci5.googleusercontent.com/proxy/VFkr93bHbGyGsKAShSjEy1Wa5c2_E1roaPHqkXAgvfFVAe-4cPZ59CKXCpY-vig5E96sY7ojsvKFiy8uAkfA564sndlRHO01J_LqgsbCJyyzudeSS78=s0-d-e1-ft#https://s3.amazonaws.com/careemcrm/promotional/careem_logo_Care.png" class="CToWUd">
Since I was using Gmail, images were not displayed directly due to a security feature. The actual image link was the one after the location hash:
https://s3.amazonaws.com/careemcrm/promotional/careem_logo_Care.png
I suspected that careem_logo_Care.png had been deleted, causing the error. When I checked the S3 bucket link, I got the following response:
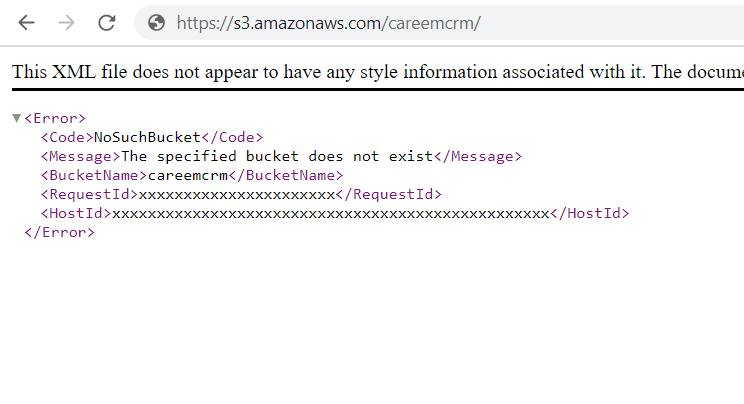
As you can see, the response indicates NoSuchBucket, which, in security terms, suggests that we can take over this bucket. And that’s exactly what happened. I used the AWS CLI with my AWS account to register the bucket. Then, I uploaded a file from my PC to the S3 bucket.
Here’s our PoC:
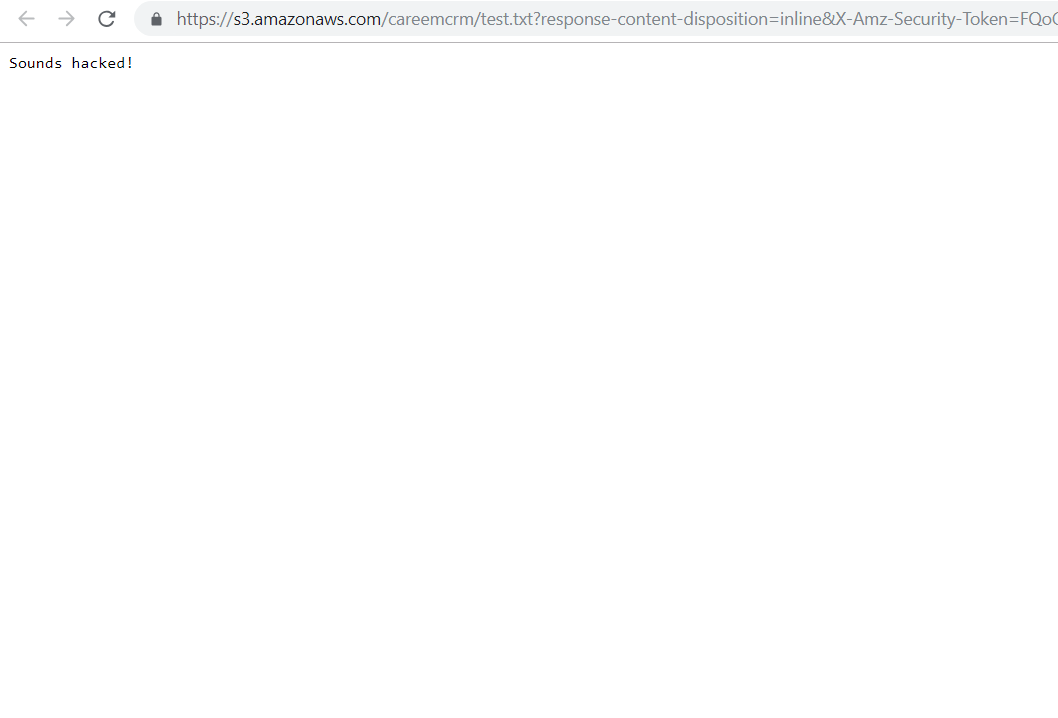
I tried to find a way to report this issue but had no luck. Careem does not have a bug bounty program, which was disappointing, given the company’s reputation.
I reached out to a friend who works at Careem’s Iraq office. He connected me with the security team, and they promptly fixed the issue. I offered to remove the S3 bucket from my account so they could reclaim it, but they said they didn’t need it anymore.
They later emailed me, confirming that they had resolved the issue. The root cause was:
Based on your initial description and proof-of-concept, this appears to be an abandoned S3 bucket that may have belonged to a former employee. As a result, no one had access to the necessary credentials.
For Bug Bounty Hunters & Security Engineers
It’s crucial to keep an eye on broken links—especially those in emails, PDFs, or old event pages. These often lead to security vulnerabilities.
URL Tracker Project!
I started a side project to track all cloud services and links that might be susceptible to takeover attacks. The project is still in progress, and you can follow it here.
What’s Next?
If you believe your site, app, or network is secure and want to verify it, feel free to contact us at contact@cube01.io.