Exploiting OAuth Vulnerabilities in Oculus
Introduction
In early 2015, while exploring bug bounty programs, I discovered that Oculus was within the scope of Facebook’s bug bounty program.
When a product is in scope, a bug bounty hunter should investigate all subdomains and main domains. At that time, the domain for Oculus was https://developer.oculusvr.com.
I noticed a menu link to https://answers.oculus.com. While browsing the site, I found that it allowed image uploads in the comments, which caught my attention.
Analyzing the Upload Process
The upload function checked if a file had an image extension, verified through the image=true parameter in the request.
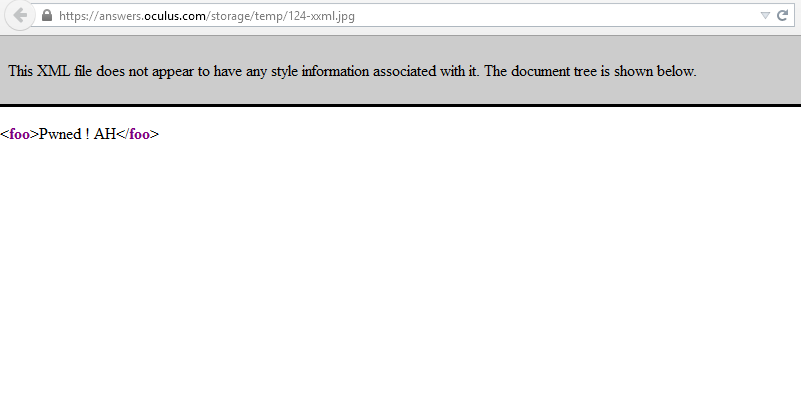
I uploaded a file named xxml.jpg and intercepted the request using Burp Suite. I modified the Content-Type to text/xml and forwarded the request.
Expanding the Attack Surface
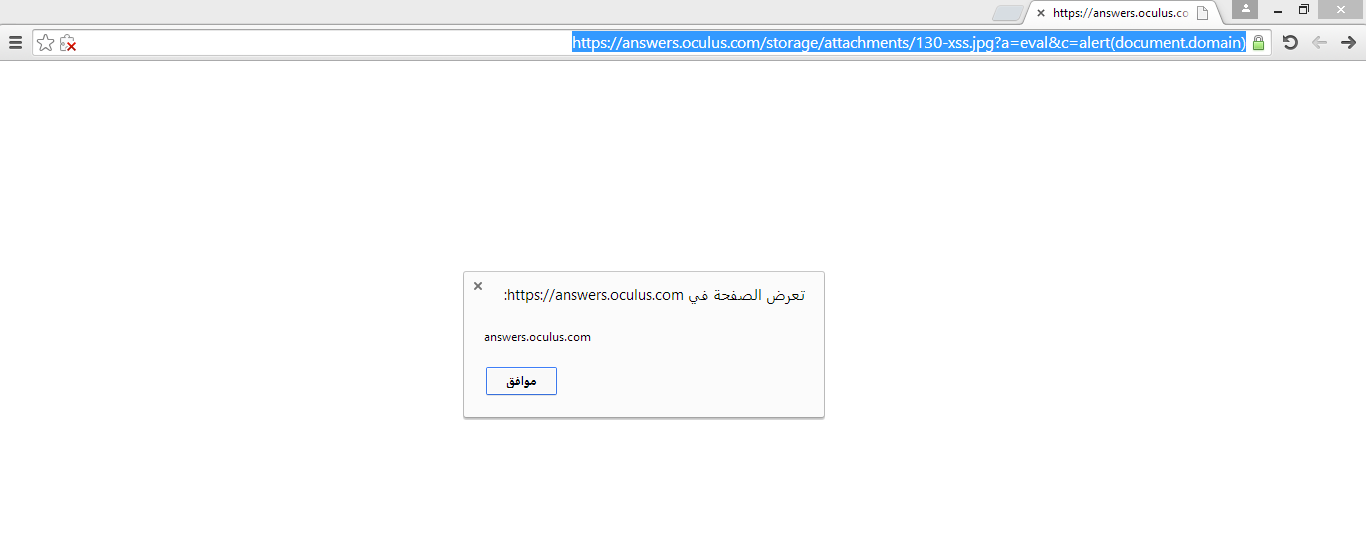
Uploading .php and .html files resulted in 500 server errors, but I sought a more effective approach. I tested SWF files, as they can be used for SOP bypass, XSS, open redirects, and CSRF token leaks. I used @evilcos’s xss.swf tool, available here.
I intercepted the request again, changed the Content-Type to application/x-shockwave-flash, and forwarded it.
The SWF file uploaded successfully.
Reporting to Facebook
I reported the issue to Facebook, expecting a response. Instead, they closed my account and replied:
Hi Abdullah,
Thank you for your report.
This subdomain is actually not part of the Facebook bug bounty program and is hosted by AnswerHub. If you believe you have discovered a security vulnerability in that site, please consider responsibly disclosing it directly to them.
Thanks,
Mark
Security
I initially assumed all Oculus domains were in scope. Disappointed but not deterred, I investigated further.
Exploiting OAuth Token Theft
I attempted logging in using api.oculus.com and discovered I could steal an access token using the uploaded SWF file.
Proof-of-Concept URL:
https://api.oculus.com/v1/oauth2/authorize?client_id=answerHub&response_type=token%20id_token&nonce=-blahblah&state=&redirect_uri=https://answers.oculus.com/storage/attachments/131-xss.jpg&country=US&locale=en_US
Due to improper validation of redirect_uri on api.oculus.com, I could manipulate it, leading to open redirects and OAuth token theft.
Reporting Again
I sent a follow-up report:
Hi Mark,
I understand that answers.oculus.com is hosted by AnswerHub, and I will report it to them. However, api.oculus.com is in scope and can be exploited using AnswerHub’s vulnerability to steal access tokens.
Logged out and open this URL, you will see the login page. When the user logs in, they are redirected to the SWF file, which steals the access token, compromising Oculus OAuth.Thanks.
Facebook’s Response
Hi Abdullah,
Thanks again for writing in. The redirect_uri validation issue onapi.oculus.comwas already known to us due to a previous report, and a fix is currently being tested.
As Mark mentioned, since answers.oculus.com is hosted by AnswerHub, the stored XSS issue is unfortunately out-of-scope. I encourage you to report it directly to them.
Thanks,
Aaron
Security
Since AnswerHub was a third-party service, I decided to investigate whether other companies used it.
Expanding the Scope to eBay and IBM
Using Google dorks, I found that eBay, IBM, and other organizations were also using AnswerHub. I repeated the same SWF upload process and confirmed the vulnerability on multiple platforms.
Affected Websites:
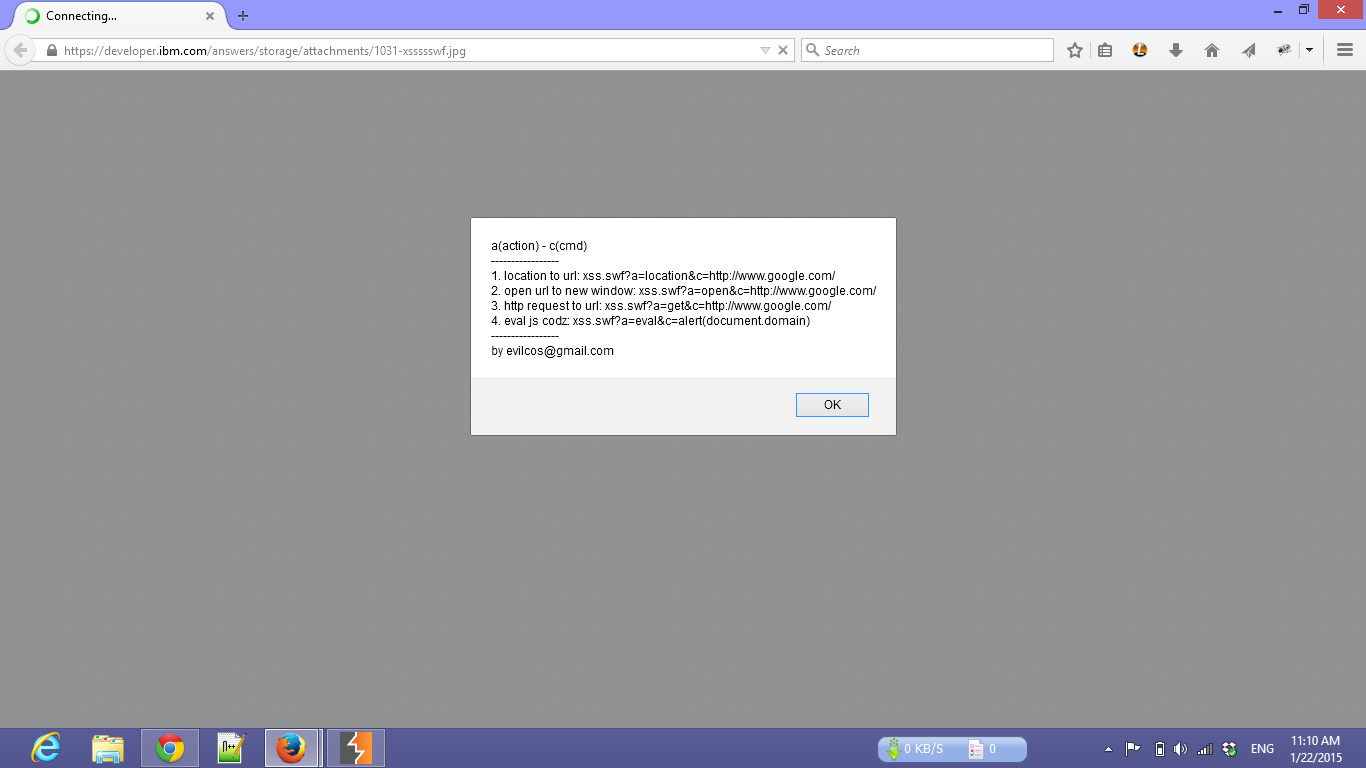
Reporting to AnswerHub
I contacted Matthew Schmidt, CTO of Dzone, the company behind AnswerHub. Since they did not offer bug bounties, they promised to send a Dzone merchandise package, which I never received.
Weeks later, AnswerHub published a release note, acknowledging the fix but without mentioning my name. After reaching out again, they added my name but misspelled my last name.
Link to Release Notes:
http://answerhub.com/releases/changelogs/answerhub-1.6.3-release-change-log/
Final Follow-Up with Facebook
I informed Facebook about the outcome, and Neal Poole replied:
Hi Abdullah,
Glad to hear it!
Thanks,
Neal
Security
Conclusion
This investigation uncovered multiple vulnerabilities affecting Oculus, eBay, IBM, and other companies due to improper OAuth validation and third-party service weaknesses.
Key Takeaways:
- OAuth misconfigurations can lead to serious security risks, including token theft.
- Third-party services can introduce vulnerabilities into otherwise secure systems.
- Google dorking is an effective technique for finding similar vulnerabilities across multiple organizations.
That’s all. Thank you for reading. Feel free to contact me on Twitter: @Abdulahhusam.